What Makes a Blockchain Secure?
- Blockchain
- Article
- 3 mins
If you own Crypto or you are thinking of buying some. You must have wondered how secure it is. One thing to note is this; the blockchain is secure under certain conditions and cannot be manipulated, but not every existing blockchain is secure.
Blockchain security is dependent on several mechanisms that include advanced cryptographic techniques. It is the underlying structure of most cryptocurrency systems and prevents digital money from being duplicated, stolen, or destroyed.
Blockchain technology is used in other contexts where data immutability and security are highly valuable. A few examples include the act of recording and tracking charity donations, medical databases, and supply chain management.
Characteristics of blockchain technology
The following are the main characteristics of blockchain.
Digital: All the information on the blockchain is digitized, thus eliminating the need for manual documentation.
Distributed: The control of a blockchain is shared among all peers in the transaction chain. Participants independently verify information without a centralized authority. Even if one node fails, the remaining nodes continue operating, ensuring no disruption.
Persistence: Blockchain will not create/persist invalid transactions as determined by consensus. Cryptographically, the blocks are sealed in the chain. It is impossible to delete, edit, or copy already created blocks and put them on the network. This leads to the creation of digital assets and ensures a high level of robustness and trust.
Chronology: Each block is like an archive that stores information about a transaction and links to the previous block in the same transaction. These connected blocks form a chronological chain providing a trail of the underlying transaction.
Consensus-based: Every transaction on a blockchain is carried out only if all the parties on the network approve it. Also, consensus-based rules can be changed to suit different circumstances.
Digital signature: Blockchain enables the exchange of transactional value using unique digital signatures that rely on public keys (decryption code known to everyone on the network). Private keys are codes known only to the owner to create a proof of ownership. This is very critical in avoiding fraud in record management.
Immutable: All the transactions are fixed in a blockchain technology-based system. Every transaction is encrypted, storing the time, date, the participants, and the hash to the previous block.
Consistent: Blockchain data is complete, consistent, timely, accurate, and widely available.
Anonymity: All users interact with the blockchain using a generated address, leaving their identity anonymous.
The role of cryptography in blockchain security
Blockchains rely heavily on cryptography to achieve security. In this context, the so-called cryptographic hashing functions are of fundamental importance.
Hashing is a process through which an algorithm (hash function) receives data and returns an output (hash) predictable and fixed in size or length. Regardless of the input size, if the input doesn’t change, the resulting hash will always be the same no matter how many times you run the hash function.
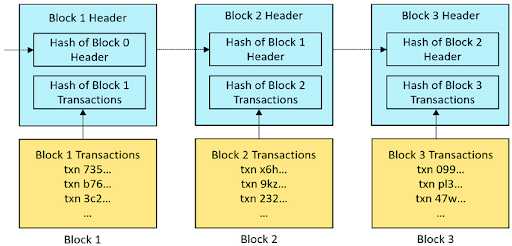
(An example of how blocks are chained to form a blockchain. Source: ResearchGate.)
However, within blockchains, output values known as hashes, are used as unique identifiers for data blocks. New blocks are generated as regards the hash of the previous block. That is what creates a chain of linked blocks. The block hash is dependent on the data contained within that block, meaning that any change made to the data would alter the block hash. These hash identifiers play a role in ensuring blockchain security and immutability.
In addition to protecting transaction records on ledgers, cryptography also plays a role in ensuring that wallets used to store cryptocurrency are safe. The paired public and private keys that allow users to receive and send payments are created through asymmetric or public-key cryptography.
Private keys are used to generate digital signatures for transactions, making it possible to claim ownership of the coins that are being sent. Asymmetric cryptography prevents anyone but the private key holder from accessing funds stored in a cryptocurrency wallet, thus keeping those funds safe until the owner decides to spend them.
A careful balance between decentralization and security is vital to building a reliable and effective cryptocurrency network.
As blockchains continue to evolve, security systems will change to meet the needs of various applications.
Closing Nuggets
A lot of questions arise when discussing blockchain networks. Aspiring investors tend to have doubts about the security of blockchain. Hopefully, with the knowledge, you have gained from this article, your fears, and doubts about the security of blockchain will be put to rest.
Was this article helpful?
Give us your feedback